BelkaCTF #3: Meet the Boss Writeup
Link: https://belkasoft.com/ctf_june/
Problem: We have the computer of a drug lord to comb through. We need to find evidence to lock him up for good this time.
1. Username
Prompt: What is the username on the imaged laptop?
Linux again? Debian this time. It’s still the same process as the last writeup. I load the image into Autopsy and navigate to the /home directory. Just one user this time: vt.
Answer: vt
2. Forums
Prompt: Which specific forums did the Boss have accounts on?
Autopsy loads any web searches it can find in Data Artifacts -> Web History. Looking at the entries, it seems Boss might have moved to the Brave browser, with searches such as “privacy browser” and visits to https://brave.com. Maybe there’ll be some more history to look through if I go looking for files associated with Brave.
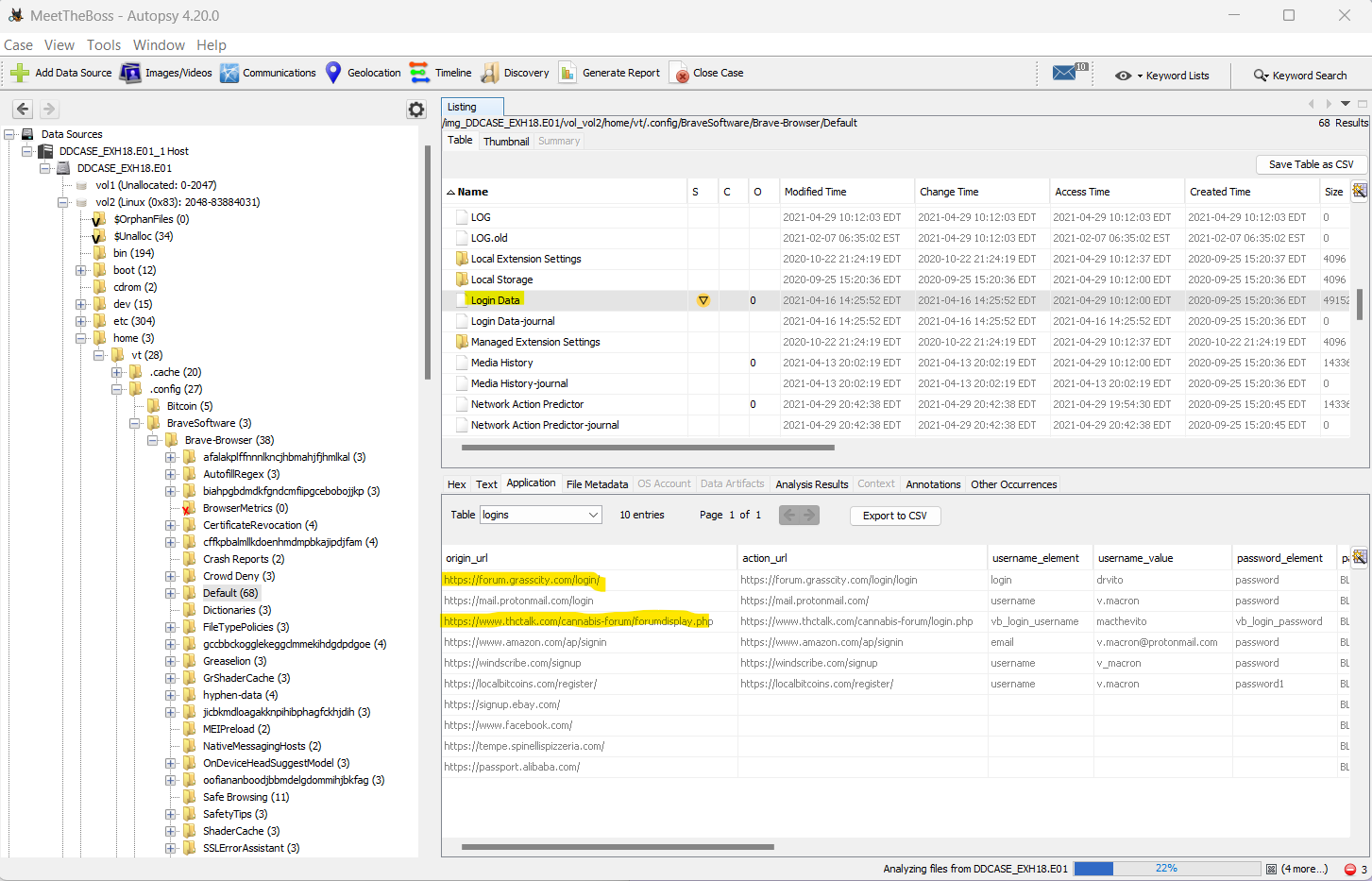
I navigate to /home/vt/.config and find a folder called BraveSoftware. I poke around a bit until I end up in /home/vt/.config/BraveSoftware/Brave-Browser/Default. Here there’s a file called Login Data which seems to be a database. In this file there’s a table called logins. Here we see sites Boss has logged into. Two forums are listed, associated with domains grasscity.com and thctalk.com.
Answer: grasscity.com, thctalk.com
3. Delivery
Prompt: What was the location where the boss had ordered a delivery to on October 19, 2020?
I look around a little more in the Default folder and come across a Web Data file, which also seems to be a database. There’s a table called autofill, and when I view the records, I see an entry for an address: 9111 W McKinley St, Tolleson, AZ 85353. There’s a timestamp for the last time it was used.
I plug it into https://www.epochconverter.com/ and confirm the address was last used on October 19, 2020.
Answer: 9111 W McKinley St, Tolleson, AZ 85353
4. Product
Prompt: What equipment has the boss ordered?
This one sucked. I looked all over the Brave-Browser/Default folder, checking every subdirectory and every file in every subdirectory. The only thing I found even a little related was a folder called databases that contained three folders: https_singin.ebay.com_0, https_signup.ebay.com_0, and https_www.ebay.com_0, with timestamps corresponding to October 19, 2020.
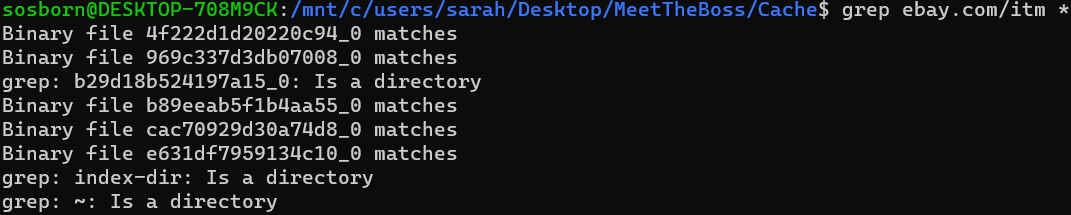
No links pointing to any items or anything, though. New lesson: when all else fails, use grep! I ended up in /home/vt/.cache/BraveSoftware/Brave-Browser/Default/Cache, which contained over 11,000 files that I did not have the patience or sanity to manually look through. So I exported the folder to my local machine, and ran grep ebay.com/itm *. And we get some matches!
Catting each of these gives the following links:
- https://www.ebay.com/itm/273997170926?hash=item3fcb8108ee:g:OaAAAOSwee5dcUNS
- https://www.ebay.com/itm/283602462421?hash=item42080626d5:g:oNkAAOSw5nZdZXlN
- https://www.ebay.com/itm/313460105738?hash=item48fbada20a:g:9o4AAOSwcMNgU6NA
The first and third links point to the same page: a listing for Pyrex Container/Tube w/ Flat Bottom Chemistry Lab Glassware.
Answer: Pyrex Container/Tube w/ Flat Bottom Chemistry Lab Glassware
5. Thumb Drive
Prompt: What thumb drive was the Boss actively using?
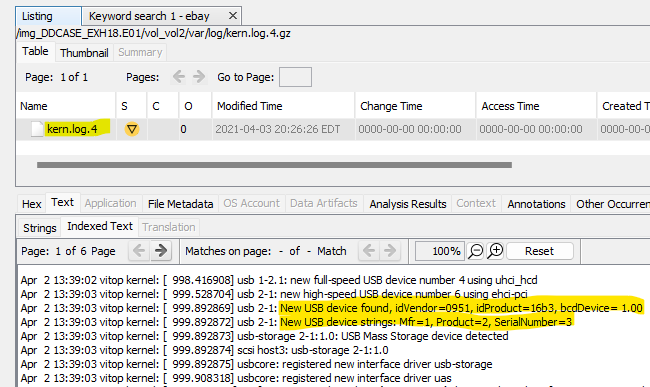
I did some light google searching and found that one might be able to see USB devices in /var/log. So I start looking through the files in Autopsy. I don’t have to look for very long this time; in kern.log4.gz there’s a file called kern.log.4. The very first few lines show a USB Mass Storage device was connected to the system.
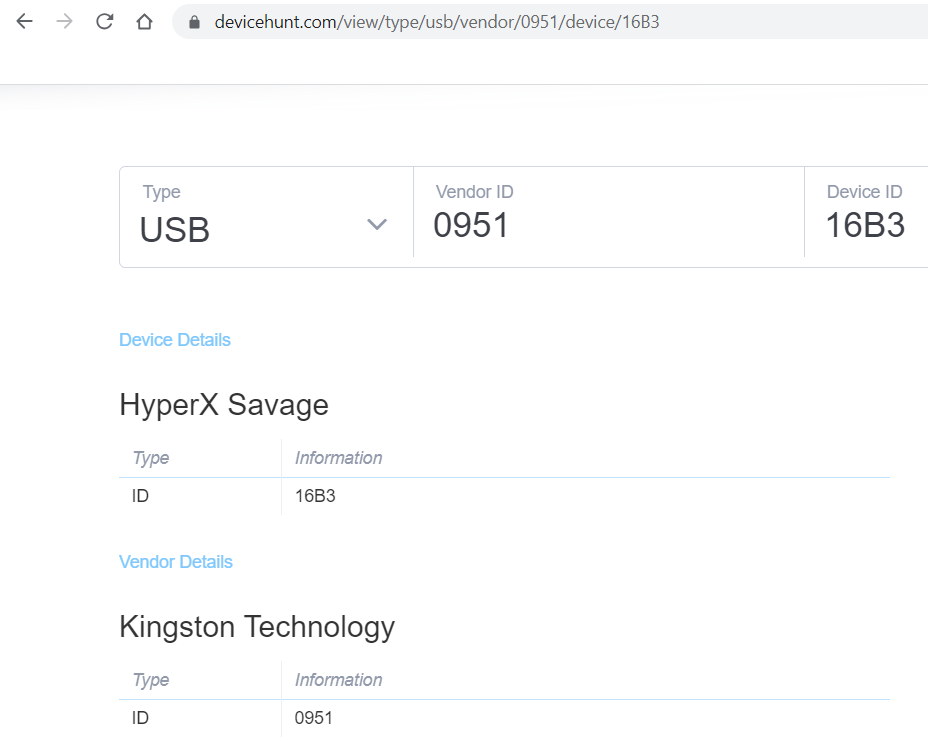
Looking up the Vendor ID and Product ID gives a make of Kingston and a model of HyperX Savage.
Googling the device gives the color: Red and Black.
Answer: Red, Black
6. CRM
Prompt: What is the URL of the Syndicate’s CRM system?
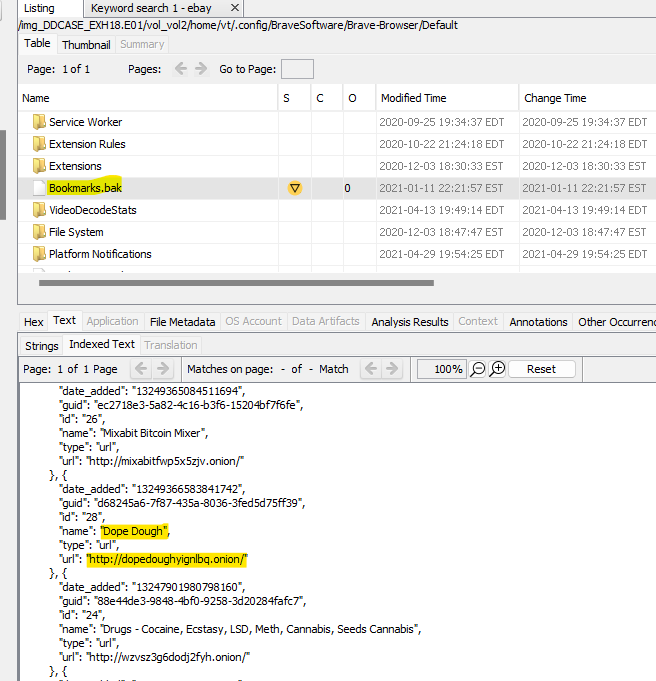
Back to Brave Browser’s Default folder! I come across a file called Bookmarks.bak that has some interesting, drug-related bookmarks in it. I recall a file named dough.dat in discovery, so of the bookmarks, I figure the most likely for a CRM would be Dope Dough at http://dopedoughyignlbq.onion.
Answer: http://dopedoughyignlbq.onion
7. Password
Prompt: What is the password to the syndicate’s CRM system?
In the autofill table from task 3 I remember seeing a field for passwords, but they’re not available in plaintext. So began a new learning objective: to mount an image as a VM to see if I can access those passwords.
I loaded the image into FTK Imager and exported it as a raw (dd) image. From there, I used VirtualBox to convert the raw image to VDI - a format VirtualBox would understand (VBoxManage convertdd image.001 image.vdi --format VDI).
Autopsy reveals the distro is Ubuntu. I create a new VM with the image as VDI. I enter into boot mode and change the password for vt by accessing root from recovery mode.
I allow the machine to finish booting up. From here, I have an option to login as vt, which I do with the password I just set.
After logging in successfully, I open the Brave Web Browser.
I click the hamburger icon in the top right, and click Settings. I scroll down until I hit the Autofill section.
I click on Passwords, which expands to show associated passwords for a few sites. Clicking the eye next to each of them reveals the plaintext.
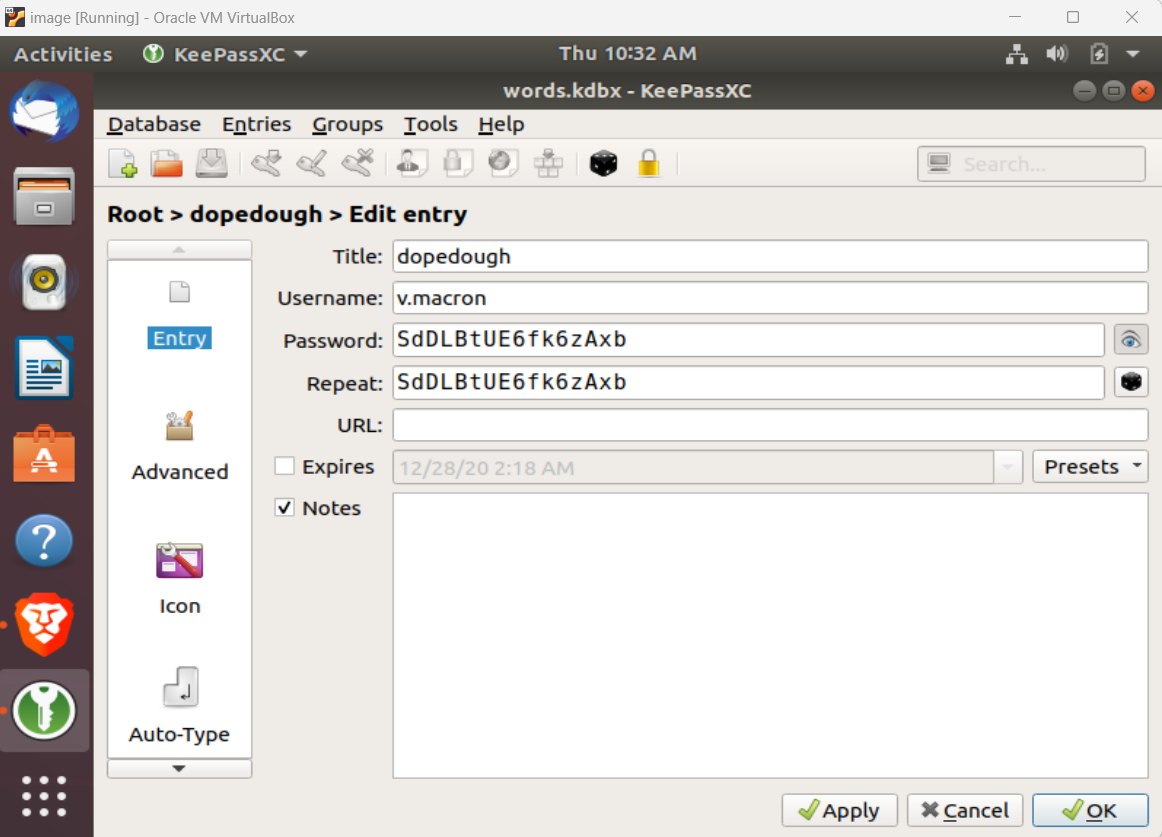
Hm, maybe one of these will open that KeePass file on the Desktop I saw (words.kdbx). Sure enough, the very first one I try opens it up to reveal more passwords, and one for dopedough.
Examining the entry gives me the password: SdDlBtUE6fk6zAxb.
Answer: SdDlBtUE6fk6zAxb
8. Big Client
Prompt: What is the name of the night club the Syndicate was providing drugs to in bulk?
I can’t log in to the CRM, because the link is no longer functional. But I can start poking around in some of his accounts. His email seems like a good place to start. I log in to Proton Mail with his credentials (which I also pull from words.kdbx) and run a search for “crm”.
Lucky me! I open the most recent and pull out the attachment: a file called backup.zip. From it, I extract a file called backup.csv. Opening this file in LibreOffice Calc (yuck), I see it contains sales records with coordinates.
The task is looking for a night club in a neighbor state. We know the boss is operating out of Arizona, which is bordered by Nevada, Utah, and New Mexico. For a nightclub, my guess would be Las Vegas, Nevada, so we’re looking for latitude 36 and longitude -115.
I write a simple script isolating out records with latitude 36 and longitude -115, rounding the coordinates to 3 decimal places, and writing to a new file.
1
2
3
4
5
6
7
8
9
10
with open("backup.csv", "r") as file:
with open("backup_2.csv", "w") as file2:
for line in file:
if("Location" in line):
continue
if("36." in line and "-115." in line):
arr = line.split(',')
arr[3] = "\""+str(round(float(arr[3][1:]),3))
arr[4] = str(round(float(arr[4][:len(arr[4])-1]),3))+"\""
file2.write(','.join(arr))
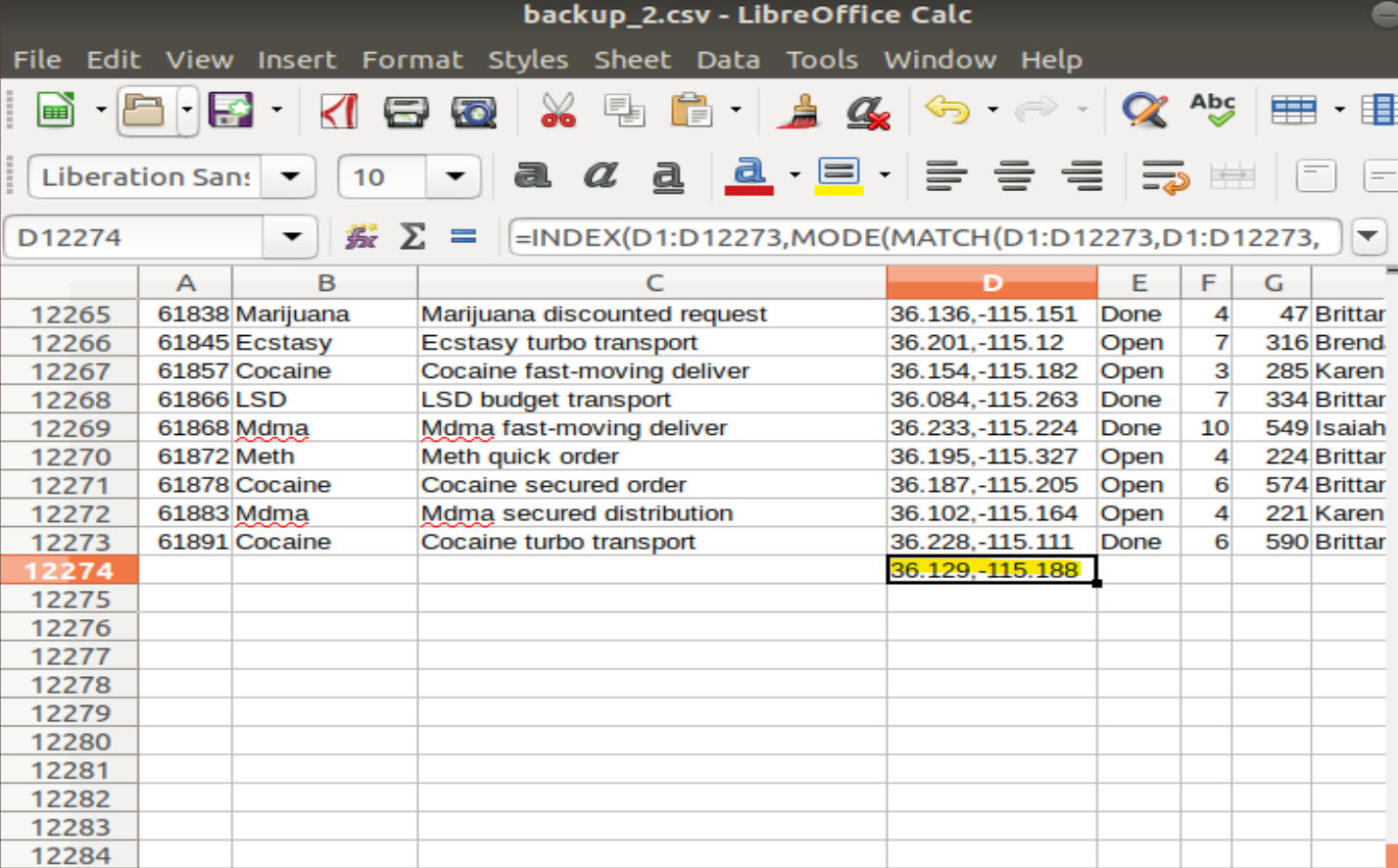
I open the new file in LibreOffice Calc and use the formula INDEX(range,MODE(MATCH(range,range,0))) to find the most frequent string of coordinates. This returns 36.129, -115.188.
Plugging these into Google Maps shows the location as Embassy Nightclub.
Answer: Embassy Nightclub
9. Hosting
Prompt: What is the IP address their CRM is hosted at?
Since the site isn’t functional anymore, maybe I could look at the email and see if I can pull the IP out of it.
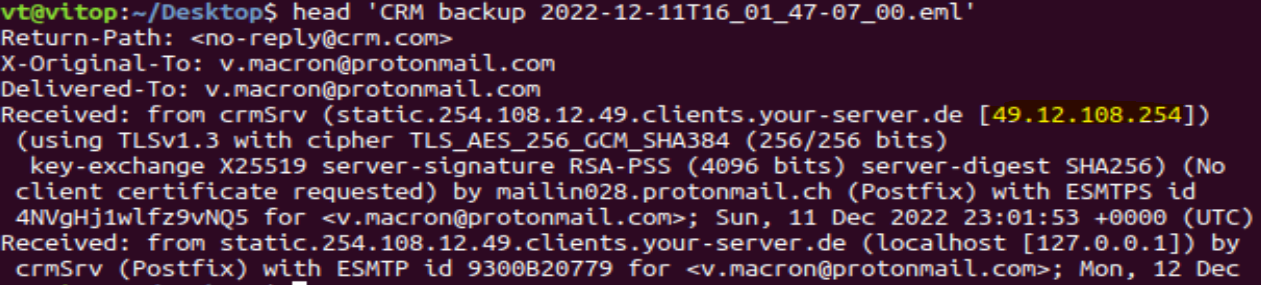
Looking at the email in Proton Mail doesn’t help me out much, so I export it to the Desktop for some Linux magic.
Running the head command gives the static IP for the CRM server: 49.12.108.254.
Answer: 49.12.108.254
10. Tranche
Prompt: What are the cryptocurrency wallet addresses the Boss had transferred salary to in the last batch? (4 of them)
There’s a file of interest in /home/vt/Documents/copy/dough_apr called wallet.dat. I export the file to my local computer. Loading the file into the Bitcoin Core app shows the transactions; the ones with labels give the addresses we’re looking for.
The addresses associated with those transactionsa re:
- 1B4uj2cMcVncGSsH7myYQF571JaojxCy4T
- 1HcZrD8gqDEtYhgmKJ2ECJAwA2stioknme
- 1FrxcR5Fj593ZbgYiiApVVEUV6PjvYfnqn
- 1NJXwLN5uC1PwWQ7yfvJiQTG76UUXTkrxr
Answer: 1B4uj2cMcVncGSsH7myYQF571JaojxCy4T, 1HcZrD8gqDEtYhgmKJ2ECJAwA2stioknme, 1FrxcR5Fj593ZbgYiiApVVEUV6PjvYfnqn, 1NJXwLN5uC1PwWQ7yfvJiQTG76UUXTkrxr
11. Retrospective
Prompt: What cryptocurrency wallets did the Boss transfer salary to in February? (4 addresses)
If we cat the wallet.dat file, we can see that there’s repeated strings “fromaccount” and “timesmart” followed by what looks like a timestamp.
There are no transactions from February in wallet.dat, but maybe there’s a trace of another wallet on the system. Autopsy lets us do a keyword search. Searching for “fromaccount” gives us a few results, a couple of which are from unallocated space.
Now we’re just looking for a timestamp for February 2021. There’s a few February timestamps in the second unallocated file.
Going back in the unallocated space a bit, we’re able to find some wallets. Pulling out the ones with labels related to February gives the four wallets we seek:
- 1GChpNsQ5x5yynwkuyXWq3Ea5JKYgdPKir
- 1CwWyNGGCjzmkuQnQRRA7H6zsUjt2Y9d8g
- 1PGLY1kFGi1RcZ4JAKY4v1VdcHJJwhY1Hs
- 19yJnHa5smr63fdDBpwrJUBCkud8J6EbSn
Answer: 1GChpNsQ5x5yynwkuyXWq3Ea5JKYgdPKir, 1CwWyNGGCjzmkuQnQRRA7H6zsUjt2Y9d8g, 1PGLY1kFGi1RcZ4JAKY4v1VdcHJJwhY1Hs, 19yJnHa5smr63fdDBpwrJUBCkud8J6EbSn
Debrief
I hated this one! It was extremely frustrating; I had to consult the writeup on pretty much every single question. What a blow to the self-confidence I’d built up over the past two CTFs. Positives to come out of this awful, awful CTF are 1) I now know that there’s so much more I need to learn, and 2) I was able to learn a lot from these tasks. I’m hoping for a bit of an easier time on the next one.